The Search Monitor Detects and Takes Down Fraudulent PPC Ad Ring
June 09, 2014
*originally published on Search Engine Land
Did you know that your paid search ads are susceptible to the same type of fraud that affects other forms of digital advertising? And we’re not just talking about click fraud here.
The fraudulent tactic affecting PPC the most dramatically these days is a fairly insidious one that can be hard to detect. It’s called PPC ad impersonation and occurs when an impostor advertiser takes a known URL, like JossAndMain.com, and uses it as the Display URL of their own advertisement.
When you first hear about PPC fraud rings, you tend to think of click fraud where an automated system, not a real person, is generating fake clicks on an advertiser’s ad. However, PPC impersonation is actually a much larger problem than click fraud, and marketers need to be watching to ensure their brand isn’t negatively impacted.
Ad Impersonation Is The New Click Fraud
Click fraud was a bigger issue in the past, but now is mostly dealt with by tighter controls from the search engines. Ad impersonation has overtaken click fraud and is now the prevalent form of fraud on PPC advertising. The search engines are only just beginning to work with vendors like The Search Monitor (full disclosure: my employer) to identify it and take it down.
In May 2014, The Search Monitor detected fraudulent PPC ads running on Bing, Yahoo, and Google. The fraudsters impersonated more than 300 advertisers on a global scale.
The fraud was not confined to any particular type or size of company. It spanned several industries, including leading businesses in automotive (JC Whitney), home furnishings (Joss & Main), software (MobiStealth), printing (Tiny Prints), home & garden (Ace Hardware), travel (BookingBuddy), firearms (Brownell’s), and services (Deluxe).
What Is PPC Ad Impersonation, AKA URL Hijacking?
PPC impersonation is also commonly known as URL Hijacking. URL Hijacking occurs when the scammer impersonates an advertiser by using the advertiser’s URL as its Display URL in PPC ads. Then, the scammer links the ads to the real advertiser’s site through an unauthorized link such as an affiliate link, a phishing link, or a cookie-stuffing URL.
Search engines only allow one ad to show at a time with the same Display URL in sponsored search listings. Therefore, URL Hijacking is costly to the brand owner by forcing the actual brand owner to compete against itself for ad placement. This unwanted activity drives up the cost per click (CPC), interferes with ROI metrics, and decreases control of ad copy messaging.
URL Hijacking typically occurs on brand and brand-plus keywords since these keywords receive higher CTRs and lower CPCs for the brand holder. Below is an example from our monitoring technology showing a Joss & Main ad that appears to be run by the advertiser, but is actually not:
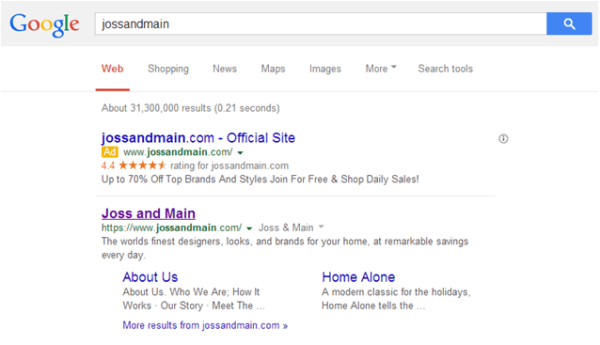
Why Is This Fraud Committed?
There are many reasons why a fraudster would want to impersonate a known brand-name advertiser. Here are the top four reasons:
1. The impersonator might be an affiliate who is engaged in direct linking. Direct linking occurs when an affiliate directs traffic from a paid search ad directly to your landing page. By direct linking from the PPC ad — through an affiliate link and then to your landing page — the affiliate can capitalize on your brand equity without having to invest in building their own high-quality landing page.Since brand holders typically enjoy a strong clickthrough rate on brand and brand-plus terms, affiliates can arbitrage their PPC campaign for a low price while driving high-quality, high-converting traffic through their affiliate link. 2. The fraudster could be a phishing site that directs traffic to a spoofed landing page to gather personal information. The spoofed landing page can look and feel like the brand holder’s website. Often, this ruse is conducted using the promise of a free gift card in exchange for an email address. 3. The fraudster could be an affiliate that is not in your affiliate program that wants to use your brand equity to push traffic through a link with the intent of dropping cookies. This practice is known as “cookie stuffing” and is nowhere near as delicious as it sounds. 4. Lastly, the fraudster could be another advertiser with a poor PPC quality score. The goal of the PPC impersonation is to seed the advertiser’s ad account with strong brands in order to capitalize on your brand equity and raise the other advertiser’s PPC quality score.
How Prevalent Is URL Hijacking?
URL Hijacking occurs constantly. A typical advertiser that is being hijacked might see that roughly 5% of their ads served are actually coming from an impostor on a regular basis.
However, when an attack is happening, the prevalence of URL Hijacking spikes to levels ranging from 20% of ads served to as much as 100%.
The two charts below show spikes in URL Hijacking observed by The Search Monitor in the clothing and retail furniture industries. The charts illustrate how fraudulent activity can appear at any time and represent a huge portion of an advertiser’s activity. Even after the fraud disappears, you can see how it can easily re-appear a few days later.
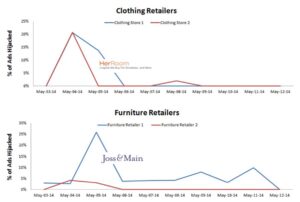
How Was The May 2014 Fraud Ring Detected?
In early May 2014, The Search Monitor discovered that more than 300 advertisers were under attack worldwide from URL hijackers. The imposters were running fraudulent ads on brand and brand-plus keywords an average of 42.5% of the time.
The low end of the range was around 10% of the time, and the high end of the range as much as 100% (i.e. every single ad seen had been overtaken by an imposter). The hijacks were perpetrated through several thousand domains used as Destination URLs of PPC ads. These domains included wileytrack.com, toppertrack.com, togateway.com, and cimjwc.com.
In some cases, the hijacker tried to look like an authentic tracking URL. For example, one hijacker was trying to impersonate Kenshoo, a widely used marketing solutions provider helping companies with marketing optimization. Normally, the Kenshoo tracking URLs contain the domain xg4ken.com. The hijacker flipped this domain around and was using x4gken.com where the ‘g’ and ’4′ were switched.
It took a team of experts to detect the full extent of this activity. The hijackers were tracked down by a three-party effort involving Rakuten LinkShare, Bing, and The Search Monitor.
The Search Monitor’s ad monitoring technology scours search engines globally on a regular basis, performs searches, and analyzes the results. When URL Hijacking is detected, the system first looks for an affiliate network link and ID. If an affiliate network link is not found, the hijacked ad is pushed to an investigations team which works with the search engine to track down the fraudster and stop the activity.
In the case of the most recent fraud bust, Rakuten LinkShare and The Search Monitor jointly discovered that the domain ‘wileytrack.com’ was impersonating several Rakuten LinkShare customers.
Here are the series of events that revealed the full extent of the fraud ring activity:
1. The Search Monitor’s investigations team noticed a spike in attack volume. At the same time, Rakuten LinkShare noticed that several of their clients were affected. Rakuten LinkShare took swift action and reported their findings to The Search Monitor.Rakuten LinkShare’s Regina Cotto explained what they saw: “We monitor affiliate search activity for our clients on a daily basis through alerts that we receive from The Search Monitor. Our team immediately noticed unexplained activity from the domain wileytrack.com across several of our clients. We worked closely with The Search Monitor’s team to uncover even more data on the nature of the fraudulent activity, data that search engines need to remove the offending companies.” 2. The Search Monitor ran a script to determine the volume of advertisers impacted and discovered that more than 300 retailers worldwide were affected, including many companies that were not Search Monitor clients. 3. The Search Monitor reported its findings to the trademark compliance team at Bing, headed by Stacie Suzuki. 4. Stacie investigated and took immediate action by removing all of the offending ads.
While the above series of events involves Bing, that search engine was not the only one impacted. Google advertisers were also affected and continue to be affected by URL Hijacking. (The Search Monitor works with Google to track down fraudsters, as well.)
Thanks to these actions, the problem was solved, at least temporarily. Many fraudsters like the ones discussed above assume that the advertisers they target do not use an ad monitoring technology to identify issues such as URL Hijacking. They hope that the sheer volume of data to analyze makes it easy to slip a few thousand fraudulent ads through the cracks of a paid search program.
Share on Social
See Our Data at Work
Provide us with a competitor’s website, a set of keywords, or one of our 1,000+ verticals, and we’ll show you the power of our monitoring capabilities. Request a personalized demo today and see what our insights can do for you!
Trusted by







 Brand Protection
Brand Protection SEM Insights
SEM Insights Affiliate Compliance
Affiliate Compliance Ad Armor
Ad Armor Learning Center
Learning Center Guides & Webinars
Guides & Webinars We Love Data™
We Love Data™ About Us
About Us Our Data
Our Data Careers
Careers Our Team
Our Team News
News Contact Us
Contact Us
